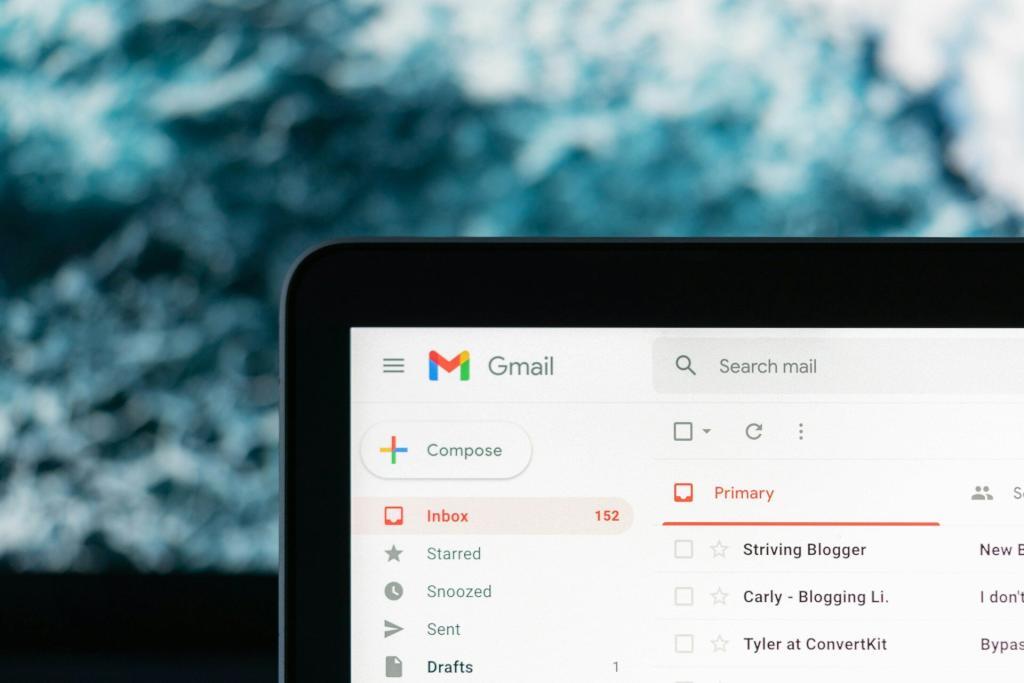
Every day, people receive emails pretending to be from trusted sources only to discover they are traps set by scammers. These emails, known as phishing attempts, trick you into giving away important personal information. Phishing attackers use clever tactics, like fake websites and alarming messages, to lure anyone off-guard into their schemes.
Staying alert and recognizing phishing attempts is the best way to protect yourself and your information. By learning what to look for, you can keep your inbox safe and ensure you aren’t a target for these cyber tricks. Understanding phishing and being prepared can keep you and your data secure.
Understanding Phishing and Its Dangers
Phishing is a deceptive tactic used by scammers to trick individuals into revealing sensitive information, such as passwords or credit card numbers. These scammers, like banks or popular websites, often disguise themselves as trustworthy sources to lower your guard. Some common phishing tactics include legitimate emails but with urgent requests to update your account details, click on a link, or download an attachment.
Falling for a phishing attempt can have serious consequences. Once scammers access your personal information, they can steal your identity, access your bank accounts, and even commit fraud in your name. For businesses, the risks are even greater, as a single phishing incident can lead to data breaches, financial losses, and damage to the company’s reputation. These outcomes highlight the importance of being vigilant and cautious with personal and professional information.
Staying alert and knowledgeable about the latest phishing tactics is essential, as these scams constantly evolve. Protecting yourself means verifying suspicious requests and avoiding giving out confidential information without confirming the source. By understanding how phishing works, you equip yourself with the knowledge to safeguard your identity and assets.
Common Phishing Techniques Targeting Small Businesses
- Deceptive Emails: Attackers send emails that appear legitimate, urging immediate action like password resets or invoice payments.
- Spear Phishing: Tailored attacks targeting specific individuals within a company, often using personal information to appear convincing.
- Clone Phishing: Duplicating legitimate emails but replacing links or attachments with malicious ones.
- Business Email Compromise (BEC): Impersonating company executives to authorize fraudulent transactions.
Recognizing Typical Signs of Phishing Emails
Identifying phishing emails can help prevent a potential cyber threat before it causes harm. Here are some telltale signs that an email might not be what it seems:
Unfamiliar Senders
Be cautious of emails from people or organizations you don’t recognize. Scammers often create emails that look similar to those of reputable companies.
Urgent Language
Phishing emails frequently use urgent language to create a sense of panic, prompting hasty actions without much thought. Phrases indicating immediate action or threats of account suspension are common red flags.
Suspicious Links and Attachments
Hover over hidden or misleading links to see the URL. Avoid clicking on links or downloading attachments from unknown or suspicious sources.
Poor Presentation and Content
Watch for emails with spelling mistakes, grammatical errors, or generic greetings like “Dear Customer.” These are often signs of a phishing attempt, as legitimate companies typically pay attention to detail in their communication.
You can identify potential threats by remaining attentive to these signs before engaging with them. This awareness is your first defense in securing your personal and professional information. Always take a moment to analyze any email that raises suspicion before proceeding.
Tools and Techniques to Attacks
Keeping your inbox safe from phishing requires both technical tools and innovative practices. Start using email filters and antivirus software to catch and remove suspicious emails before they reach you. Many email services offer built-in filters that can automatically send suspected phishing emails to your spam folder. Antivirus software adds another layer of protection by warning you about dangerous links and attachments. We use several services for our clients that provide this type of protection for as little as $5 / month/mailbox.
It is also crucial to regularly update your email settings. Ensure your spam filter settings are enabled and configured to catch unwanted emails. Enable two-factor authentication whenever possible. This feature requires you to confirm your identity using another device or app, making it harder for scammers to access your account.
Training and awareness are equally important. Educate yourself and others about the latest phishing trends and how to identify them. Regular training sessions can help reinforce what to look for and what steps to take if you encounter a suspicious email. Create a habit of checking emails thoroughly before clicking any links or sharing personal information. Being aware and prepared dramatically lowers the risk of becoming a phishing victim.
To summarize this info, here are some Effective Strategies to Prevent Email Phishing Attacks
- Employee Training: Regularly educate staff on identifying phishing attempts, such as checking for inconsistencies in email addresses and avoiding unsolicited links. Most cybersecurity insurance policies require this training at least once every year. We provide this training for our clients as a Lunch and Learn session. This can also be done by watching training videos.
- Implement Multi-Factor Authentication (MFA): Adding an extra verification step reduces the risk of unauthorized access to prevent scammers from logging into company mailboxes.
- Use Advanced Email Filters: Deploy spam filters to detect and quarantine suspicious emails before they reach inboxes.
- Keep Software Updated: Ensure all systems and applications are up-to-date to patch vulnerabilities that attackers might exploit. Ask us how we can automate and manage this for you.
- Establish Clear Policies: Define protocols for handling sensitive information and verifying unusual requests, especially those involving financial transactions. This is one of the suggestions we make to our clients is to have a “verbal authorization” requirement in place for any email requests for money transfers or the purchase of any debit or gift cards. Before the person does what is asked in the email, they contact the sender and verbally confirm the instructions. This simple process has saved several of our clients from getting scammed and money taken.
Steps to Take If You Suspect a Phishing Attempt
If you encounter a suspicious email, it’s important to act carefully. Here’s a checklist of steps to follow:
1. Do Not Click Links or Download Attachments: Avoid interacting with any links or attachments in the email.
2. Verify the Source: Contact the sender through another communication method to check if the email is legitimate.
3. Report the Email: Use the “Report Phishing” option in your email client or forward the email to a phishing reporting address provided by your email service.
4. Delete the Email: Once reported, delete the email from your inbox and trash folder.
5. Change Your Passwords: If you’ve clicked a suspicious link or engaged with the content, change your passwords immediately and use strong, unique passwords for each account.
6. Monitor Your Accounts: Regularly check bank statements and online accounts for unauthorized transactions or changes.
By following these steps, you can reduce the harm done by phishing attempts and protect your information. Acting quickly and decisively is key to maintaining your digital security and ensuring that potential threats are minimized.
The Role of Managed IT Services in Phishing Prevention
Partnering with a managed IT service provider offers small businesses access to advanced security measures and expertise. These providers can monitor networks for suspicious activities, manage regular software updates, and provide ongoing employee training. By leveraging their resources, small businesses can implement robust defenses against phishing attacks without the need for extensive in-house IT infrastructure.
Real-Life Examples of Phishing Attacks on Small Businesses
Consider a small accounting firm that received an email appearing to be from a trusted client requesting a funds transfer. The email was a sophisticated phishing attempt, and without proper verification protocols, the firm could have suffered significant financial loss. This scenario underscores the importance of vigilance and comprehensive security measures.
Additional Resources and Tools for Phishing Prevention
- Phishing Quiz: Test your ability to spot phishing attempts with Google’s Phishing Quiz.
- Security Awareness Training: Organizations like KnowBe4 offer comprehensive training programs to educate employees on cybersecurity best practices. Ask us about which ones we use and believe are the best for your employees.
- Email Authentication Protocols: Implement protocols such as SPF, DKIM, and DMARC to verify the legitimacy of incoming emails.
By proactively implementing these strategies and leveraging the expertise of managed IT services, small businesses can significantly reduce the risk of falling victim to email phishing attacks. Protecting your company’s data and maintaining the trust of your clients is paramount in today’s interconnected world.
For more information on enhancing your business’s cybersecurity posture, explore our Managed IT Services and learn about our Cybersecurity Solutions.
Conclusion
Understanding and preventing phishing threats is essential in safeguarding your personal and professional information. By recognizing the tactics scammers use and how to spot suspicious emails, you can better defend against these threats. Taking proactive measures, like utilizing email filters and updating your security settings, builds a stronger wall of defense around your data. Incorporating training and awareness into your routine educates you and others, reducing the risk of falling for these scams.\
Trinity Solutions Inc. is here to empower you with managed IT services in North Carolina you need to stay protected from phishing and other cyber threats. Let us assist you in creating a safe and secure digital environment, ensuring peace of mind. Trust our team to provide you with advanced solutions tailored to your needs. Contact us today to learn how to strengthen your defenses and protect your valuable information.